Fix: Securely Connect RemoteIoT VPC AWS Not Working - Troubleshooting
Is your "securely connect remote IoT VPC AWS" setup stubbornly refusing to cooperate? The failure to establish a secure and reliable connection between your remote IoT devices and your AWS Virtual Private Cloud (VPC) can cripple your operations, leading to data loss, security vulnerabilities, and ultimately, project failure. This article delves into the complexities of this critical challenge, offering a practical guide to diagnosing and resolving the issues that prevent seamless connectivity.
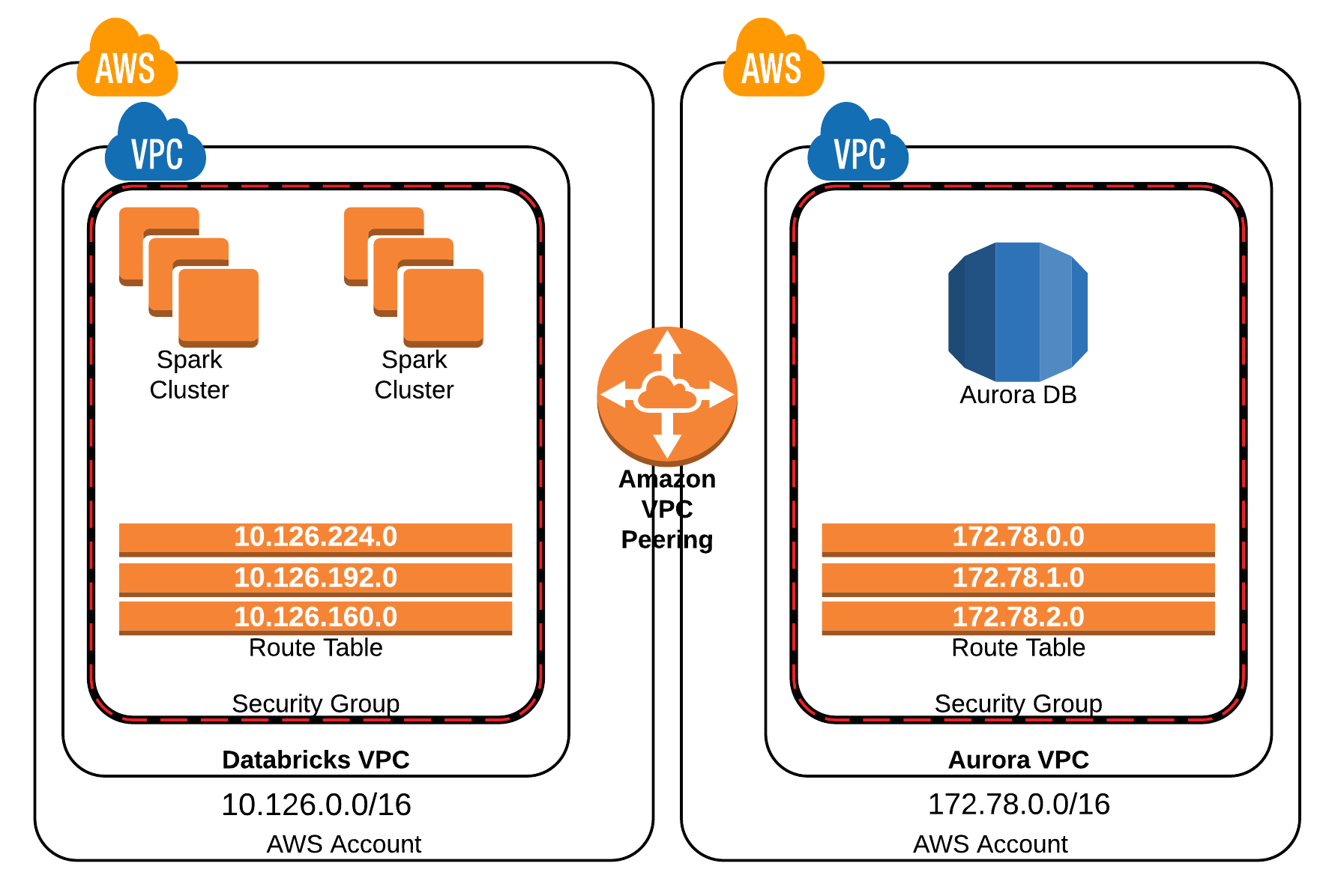
The modern landscape of the Internet of Things (IoT) is characterized by its vastness and complexity. We are witnessing an explosion in the number of connected devices, generating unprecedented amounts of data. Much of this data originates from remote locations, requiring secure and reliable connectivity to central processing and storage resources, often residing within an AWS VPC. Setting up this connection, however, is far from trivial. Numerous factors can disrupt the communication flow, from misconfigured security groups and network access control lists (ACLs) to routing issues and improperly configured VPN tunnels. Understanding and addressing these potential pitfalls is paramount to ensuring the integrity and availability of your IoT data.
Let's consider the core components that contribute to this challenge. Remote IoT devices, by their very nature, are often deployed in environments with limited network resources and potentially unreliable internet connectivity. These devices need to securely transmit data across the public internet to reach your VPC. The VPC, a logically isolated section of the AWS Cloud, provides the security and isolation necessary for your data and applications. The task then becomes how to bridge the gap between these two disparate worlds. This generally involves technologies like Virtual Private Networks (VPNs), which encrypt the data in transit, ensuring confidentiality and protecting against unauthorized access. Furthermore, the architecture must address scaling, ensuring that the connection can accommodate a growing number of devices without compromising performance or security. Failure to properly consider each of these elements can result in connectivity issues.
One of the most common stumbling blocks involves the use of AWS resources themselves. Misconfigured Security Groups act as virtual firewalls, controlling inbound and outbound traffic to your VPC resources. Network ACLs function as another layer of security, governing traffic at the subnet level. Correctly configuring these two elements is absolutely crucial, but the complexity of the configurations, and lack of knowledge can lead to errors. Then there is the matter of the network itself. Routing tables must be precisely configured to direct traffic from the remote IoT devices through the secure tunnel and into the correct subnets within your VPC. In addition, any existing on-premises network that is also intended to be connected to the VPC must be properly integrated. Finally, there are the challenges associated with securing the devices themselves. Ensuring the security of each individual device is critical, as a compromised device can create a significant vulnerability.
A deep dive into each of these areas will help illustrate the potential failure points and their solutions. One of the most fundamental steps in debugging a problematic AWS VPC connection is understanding the network topology. This begins by visualizing your environment, including the location of your remote devices, the subnets within your VPC, the VPN endpoints (if you're using a VPN), and any other relevant network components. AWS provides a range of tools, such as VPC Flow Logs, to give you visibility into network traffic patterns. VPC Flow Logs captures information about the IP traffic flowing to and from network interfaces in your VPC. This valuable data can be used to identify potential bottlenecks, security group rule violations, and routing issues.
To ensure a successful connection, it is essential to thoroughly test each of the network components. Start with the basics: can your remote devices ping the VPN endpoint's public IP address? If not, there might be a fundamental network connectivity problem on the device's side. Once basic connectivity is confirmed, you can then move on to more sophisticated tests, such as testing the VPN tunnel itself. Verifying that the VPN tunnel is up and running and that traffic is flowing through it requires the appropriate configuration settings in both the VPN server and the IoT device. You might use tools like `tcpdump` or `Wireshark` to capture and analyze network packets, helping you to verify that your data is being encrypted and decrypted correctly. These detailed checks are essential for isolating the root causes of connectivity issues.
Security is of utmost importance when it comes to IoT devices, as these devices are often deployed in environments with little or no physical security. Therefore, protecting their data is absolutely vital. AWS offers several security services that can be integrated into your IoT architecture. Services such as AWS IoT Core provides device management and security features. Further, integrating these with your VPC's security features enables you to create a robust and secure network. Consider using the features of the AWS Certificate Manager to secure communications between your devices and the cloud, as well. This will help mitigate risks and safeguard data.
The choice of VPN solution is critical. The AWS Site-to-Site VPN service is a managed service that simplifies the process of establishing a secure connection between your on-premises network or remote devices and your VPC. It handles much of the underlying complexity of VPN setup and maintenance, making it a good option for many use cases. Alternatively, you can implement a software-based VPN solution using tools like OpenVPN or strongSwan, or third-party solutions. While more flexible, these solutions require greater expertise to configure, manage, and secure. The choice depends on your technical resources and your specific requirements.
Addressing the challenges of "securely connect remote IoT VPC AWS not working" often entails troubleshooting a complex array of potential problems. However, by following a methodical and well-defined approach, you can often pinpoint the underlying issues and implement effective solutions. The key lies in a clear understanding of your network architecture, meticulous configuration of AWS services, and diligent testing. Only through rigorous and systematic troubleshooting will you be able to resolve the connectivity issues that prevent your IoT devices from communicating securely and reliably with your AWS VPC.
One common issue is related to routing configurations. Within your VPC, routing tables are the "traffic cops" that direct network traffic to its destination. If the routing tables are misconfigured, traffic from your remote IoT devices may not be able to reach the intended resources within your VPC. To address this, verify that the route tables associated with your subnets correctly point traffic destined for your remote network (e.g., the network where your IoT devices reside) to the VPN gateway. Also, ensure that there are corresponding routes on the remote side, pointing traffic back to your VPC through the VPN tunnel. Use AWS's built-in tools to diagnose these routing problems.
Another area to investigate is the security groups. Security groups act as virtual firewalls for your EC2 instances and other resources within your VPC. They control the inbound and outbound traffic allowed to and from these resources. If the security group rules are too restrictive, they might block traffic from your remote IoT devices, preventing them from connecting. Double-check the security group rules associated with the instances or other resources that your IoT devices need to access. Make sure that these rules allow inbound traffic from the IP addresses of your remote devices, and that they allow the necessary ports (e.g., port 22 for SSH, port 80 or 443 for HTTP/HTTPS) to be open.
Moreover, Network Access Control Lists (ACLs) offer an additional layer of security. Network ACLs are an optional layer of security for your VPC that acts as a firewall for all inbound and outbound traffic at the subnet level. By default, network ACLs allow all traffic, but you can configure them to deny or allow traffic based on rules similar to security group rules. If your network ACLs are configured to deny traffic, this could prevent traffic from your remote IoT devices from reaching your resources in your VPC. Check your network ACLs to make sure they are configured to allow traffic from your remote IoT devices.
Additionally, consider the device itself. Ensure that each of your IoT devices is correctly configured to use the VPN, and that they trust the appropriate certificates, if you are using them. Poor device configurations can cause traffic issues. Verify that each device has the appropriate network settings, including the correct IP addresses, subnet masks, and gateway addresses. Also, verify that the devices are configured to use a DNS server that can resolve the hostnames of your VPC resources. If you're using a software-based VPN solution on the devices, carefully review the VPN configuration files to make sure they are configured properly.
The scale of your deployment will impact performance. As your number of IoT devices grows, you might encounter performance bottlenecks. These bottlenecks can affect the security and availability of your data. Consider that the capacity of your VPN connection can become overwhelmed. The VPN tunnel has a maximum throughput, and if your IoT devices generate too much traffic, the tunnel might become saturated, leading to slow performance or dropped packets. Scaling your VPN connection means increasing the capacity of the VPN. AWS offers multiple VPN options, including Site-to-Site VPN and AWS Client VPN, and you can use multiple VPN gateways to increase throughput. Load balancing can also be implemented across multiple VPN connections.
Data transfer costs are also something to consider. When data is transferred over the VPN, there will be associated costs for data transfer out of the VPC. Be sure to understand the pricing structure for your chosen services and optimize your architecture to minimize these costs. One way to reduce costs is to compress the data before sending it from the IoT devices. This reduces the amount of data that needs to be transferred over the VPN. Also, consider batching data uploads from the IoT devices. Rather than sending small pieces of data frequently, you can have your devices send data in larger batches at regular intervals. This reduces the number of connection attempts, and also can reduce data transfer costs.
The reliability of your network is paramount to the overall success of your project. Ensure the connectivity to your remote IoT devices is reliable. Regular monitoring and preventative maintenance are essential to identify and address any issues before they escalate. Implement proactive monitoring to detect connectivity problems or other anomalies. Use tools such as CloudWatch to monitor metrics such as VPN tunnel status, CPU utilization of your EC2 instances, and network latency. Configure alerts to notify you immediately of any problems. Further, perform routine maintenance on your VPN connections. This maintenance might involve updating the VPN software, renewing certificates, or reviewing the configuration of the VPN gateways and the remote device setup.
Debugging these connections can be a process of elimination. Start by checking the most basic components and move to more complex configurations. If the remote IoT devices cannot ping the VPN endpoint, this is a symptom of a fundamental network connectivity problem, possibly on the devices side. Check the device's internet connection and DNS settings. Once basic connectivity is confirmed, proceed to testing the VPN tunnel. Use the various AWS provided diagnostic tools to troubleshoot your VPN and VPC configurations. These tools include the AWS CLI and the AWS Management Console.
The success of securely connecting your remote IoT devices to your AWS VPC hinges on meticulous attention to detail, a robust understanding of network fundamentals, and a thorough understanding of the capabilities of AWS services. While the initial setup might seem daunting, the rewards, including a secure and reliable flow of data from your devices, make the effort well worth it. Through diligent troubleshooting, proactive monitoring, and a commitment to security best practices, you can unlock the full potential of your IoT deployments.