Download Now: Remote IoT Device Software Updates & More
Is the seamless deployment of software updates to your remote IoT devices proving to be a persistent challenge? The efficiency and security of "remoteiot device software download" are not just technical considerations; they are fundamental to the operational reliability, scalability, and ultimately, the success of any IoT deployment.
The phrase, "remoteiot device software download," has become a cornerstone of modern IoT operations, yet its implementation can be fraught with complexities. From the initial design and implementation to the ongoing maintenance and security considerations, the process is far from trivial. Ensuring that the correct software version is deployed to the intended device, while maintaining data integrity and minimizing downtime, requires careful planning and execution. This article delves into the critical aspects of remote IoT device software download, exploring the technological underpinnings, the security considerations, and the best practices that can transform a potential headache into a streamlined and reliable process.
The evolution of IoT has witnessed an explosion in the number of connected devices, spanning industries from healthcare and manufacturing to smart homes and agriculture. This growth has placed an unprecedented demand on the ability to update these devices remotely. The alternative physical access to each device for software updates is often impractical, expensive, and time-consuming. Remote software download provides the lifeline, allowing for bug fixes, security patches, new feature implementations, and overall performance improvements without the need for on-site visits.
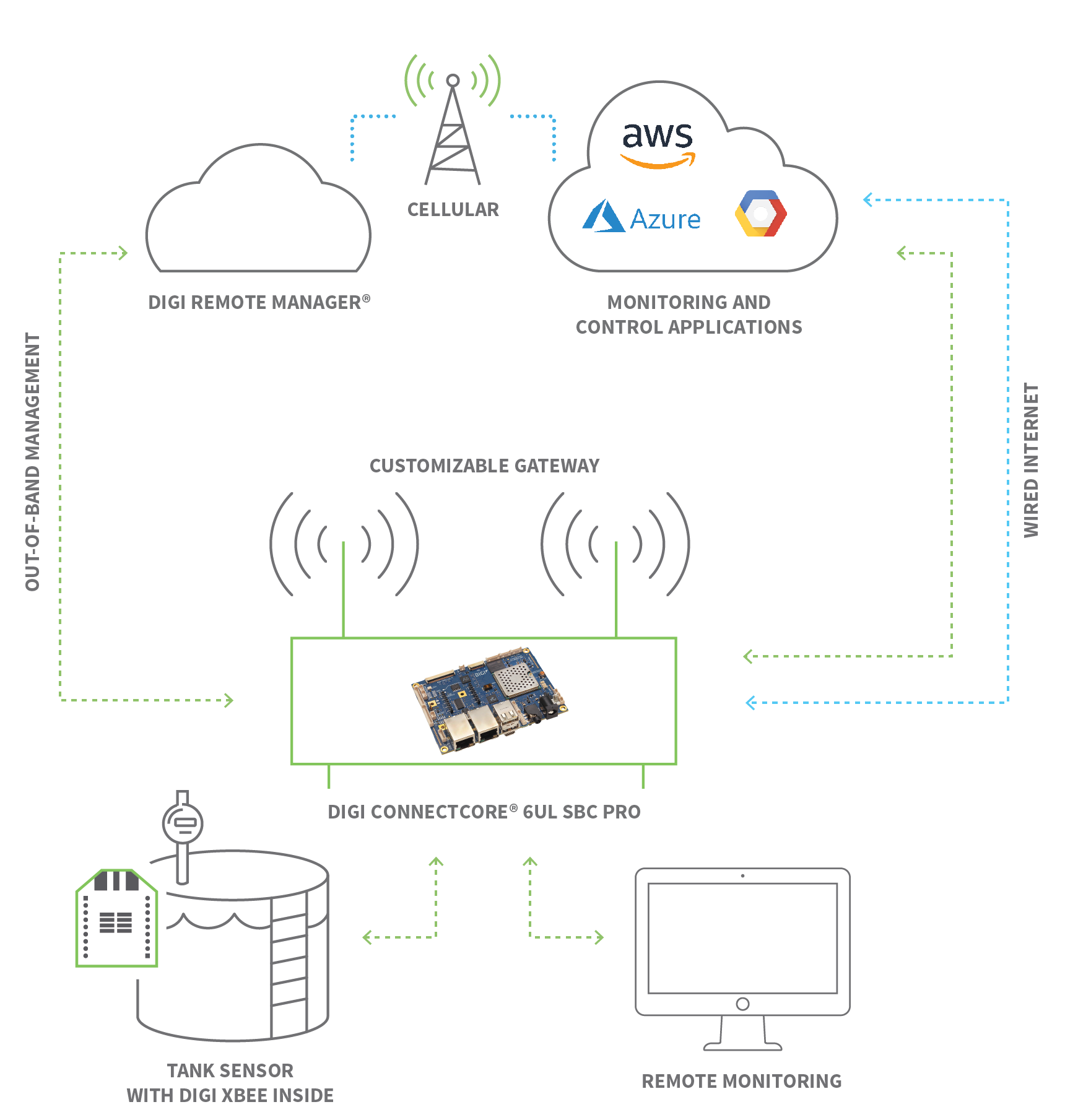
The architecture of a remote software download system typically involves several key components. Firstly, there's the device itself, which is the target of the software update. Then, there's the software update server, which acts as the central repository for the software updates. A communication protocol, often based on protocols such as MQTT, CoAP or HTTP, facilitates the transfer of the software from the server to the device. A bootloader on the device, responsible for initiating the update process, is crucial, as well as an update agent, managing the download, verification, and installation of the new software. Over-The-Air (OTA) updates is a term that's closely related, and often used interchangeably with "remoteiot device software download."
The design of a robust remote software download system must consider several critical factors. Security is paramount; software updates can be a prime target for malicious actors, aiming to compromise the device or the network. Authenticating the software packages, ensuring the integrity of the downloaded software, and encrypting the communication channel are essential steps in mitigating security risks. Version control is another important consideration. Managing multiple software versions across a large fleet of devices requires a well-defined versioning strategy and a system to track the status of each device's software version.
The process of a remote software download usually begins with the software update server receiving a new software version. The software is then packaged, often with metadata such as the target device type and the version number. The package is then cryptographically signed to ensure its authenticity and integrity. The server then publishes the update to the target devices. Once a device detects the availability of a new update, it downloads the software package. Prior to installation, the device verifies the signature and integrity of the downloaded software. If the verification is successful, the devices bootloader then takes over the installation, typically writing the new software to flash memory. Once the update is complete, the device reboots, running the newly installed software.
The selection of a suitable communication protocol is a pivotal design decision. The protocol needs to balance several factors, including efficiency, reliability, and security, while working within the constraints of the device's resources and network environment. MQTT (Message Queuing Telemetry Transport) is a popular choice for its lightweight nature and publish-subscribe architecture, which is well-suited for unreliable networks. CoAP (Constrained Application Protocol) is another option, designed specifically for constrained devices and networks. HTTP, while more resource-intensive, can be used if the device has sufficient processing power and network bandwidth. The choice of a protocol can significantly impact the power consumption of the device and the overall reliability of the update process.
Device compatibility is a critical consideration. The software update process must be designed to work seamlessly across the diversity of devices in the field. This often involves creating specific software packages for each device type and version. The use of a device management platform can greatly simplify this process, by providing a centralized interface to manage device profiles, group devices, and deploy updates. The platform can also provide detailed reporting on the status of each device and the progress of the updates.
Security is at the forefront of the remote software download process. Its an area where vigilance is non-negotiable, and the potential consequences of a breach can be significant. Encryption, authentication, and integrity checks are the pillars of a secure system. End-to-end encryption ensures that all communication between the update server and the device is encrypted, safeguarding sensitive data from prying eyes. The authentication process verifies the identity of the software package and the device. This can involve digital signatures, which allows the device to confirm that the software package comes from a trusted source and has not been tampered with. Integrity checks, such as checksums or hash functions, confirm that the downloaded software is complete and has not been corrupted during the download process. The use of secure bootloaders, which verify the integrity of the software before execution, is another crucial security measure.
Over-the-air (OTA) updates, essentially synonymous with remote software downloads in the IoT context, demand the design of a resilient update process. The system should be designed to handle network interruptions and power outages gracefully. The device should be able to resume the download process from where it left off if the connection is lost. A mechanism to roll back to the previous software version if the update fails is another critical feature. This helps to minimize the risk of bricking a device rendering it non-functional. A well-defined rollback procedure is often a vital part of the update strategy.
Testing is absolutely paramount for a successful software deployment. The thorough testing of the update process on a representative sample of devices before the actual deployment is essential. Testing should include functionality testing, security testing, and performance testing. The functionality testing ensures that the updated software works as expected, security testing confirms that the update process is secure, and performance testing assesses the impact of the update on the device's performance, such as the battery life and the processing speed. Simulation environments that closely mimic the target environment can be used to test the software download process. Canary deployments, where the update is first rolled out to a small group of devices before wider deployment, can also assist with identifying any potential problems before the full-scale deployment.
The choice of tools and technologies plays a significant role in the efficiency and reliability of the remote software download process. Several open-source and commercial solutions are available, offering a range of features from simple update deployment to comprehensive device management capabilities. Choosing the right solution depends on the specific needs of the IoT deployment. Consider factors such as the device type, the network environment, the security requirements, and the existing infrastructure when evaluating different options.
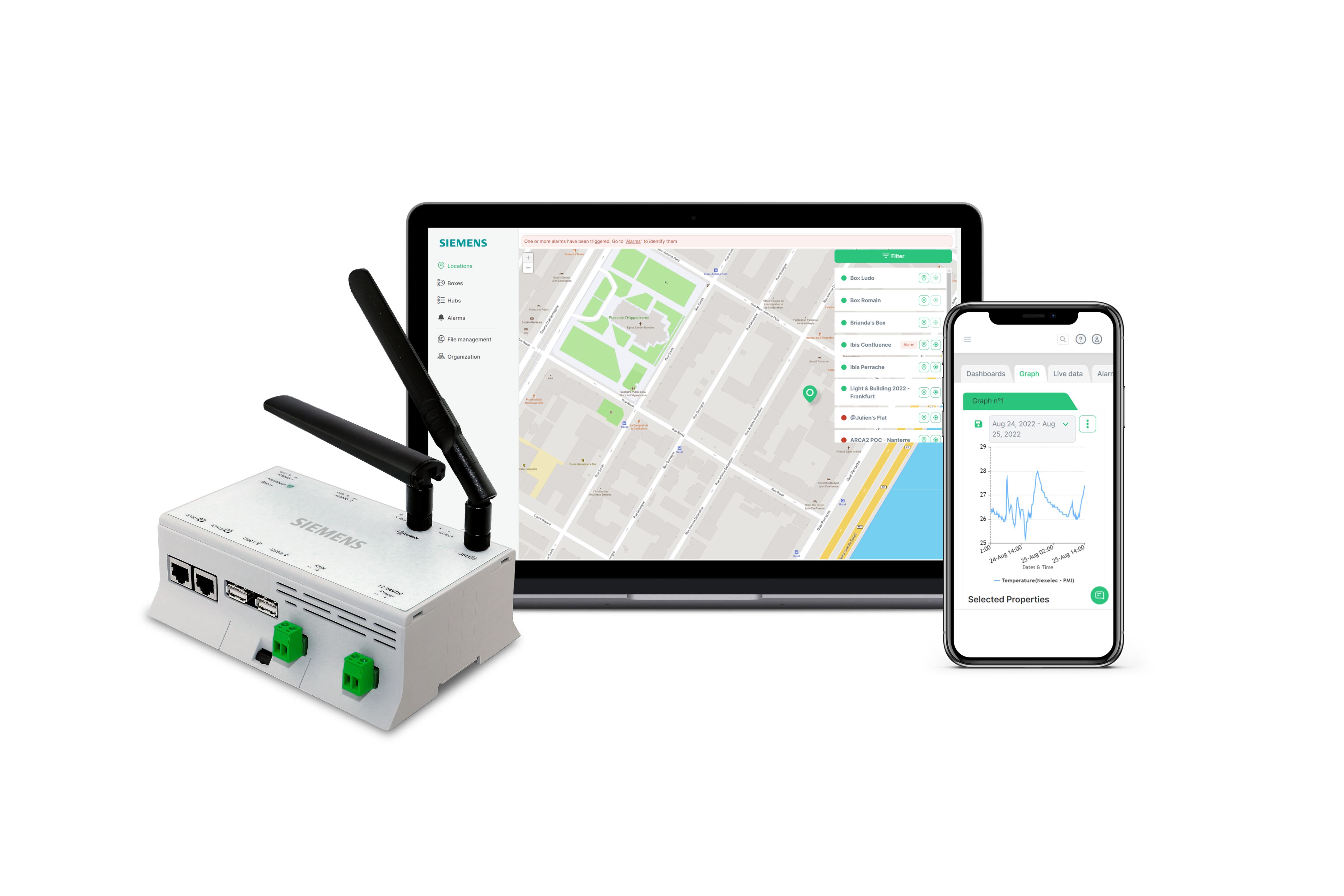
Device management platforms provide a centralized interface for managing and monitoring the entire update process. These platforms can help to streamline the deployment of software updates, track the status of each device, and provide valuable insights into the overall health of the IoT deployment. The features offered by these platforms can include device provisioning, remote monitoring, software update management, and security management. These platforms can often integrate with cloud services, simplifying the integration of the IoT deployment with other enterprise systems.
The selection of a reliable and secure over-the-air (OTA) update mechanism is essential. OTA mechanisms are designed to be robust, reliable, and secure, incorporating features such as secure bootloaders, encryption, and error handling. The availability of a reliable OTA mechanism can greatly simplify the remote software download process, reducing the time and effort required to manage the software updates.
Data integrity is another major aspect of remote software download. Ensuring that the data remains intact during the transfer process is critical to the reliability of the system. This requires the use of checksums, cryptographic hashes, and other methods to verify the integrity of the downloaded software packages. The use of secure communication protocols, such as HTTPS or TLS, also helps to protect data integrity during transit. Any compromise of the software package would potentially introduce vulnerabilities into the deployed system.
Scalability is another core concern. As the number of connected devices grows, the update process must be able to scale accordingly. The update server, the communication protocol, and the device firmware must all be designed to handle a large number of concurrent downloads. The use of content delivery networks (CDNs) can help to distribute the software updates geographically, reducing the load on the update server and improving the download speed.
Remote software download is an ongoing process that requires continuous monitoring and optimization. The performance of the system should be monitored regularly, and adjustments should be made as needed. Logs provide valuable insights into the update process, allowing the developers and the operators to identify any problems or bottlenecks. The analysis of the logs can provide insights into the performance of the system, the types of errors that are occurring, and the overall health of the IoT deployment. Gathering feedback from the devices and the operators can help improve the overall process.
The future of "remoteiot device software download" will likely be shaped by several key trends. The increased use of artificial intelligence (AI) and machine learning (ML) could enable the automation of the update process, making it more efficient and intelligent. Over-the-air (OTA) updates will become increasingly commonplace as the number of connected devices increases. The security landscape will evolve with the rise of new threats, requiring more sophisticated security measures to protect the devices and the networks. The integration of edge computing could allow the software updates to be processed closer to the devices, improving the download speeds and reducing the latency. The continued growth of IoT will necessitate the evolution of remote software download technologies, ensuring that they remain secure, efficient, and reliable.
In conclusion, "remoteiot device software download" is a critical element in the management and maintenance of any IoT deployment. By understanding the technical underpinnings, the security considerations, and the best practices, organizations can develop and implement a robust and reliable update process. The ability to update software remotely is essential for the long-term success of IoT deployments, enabling organizations to deliver new features, improve performance, and secure their devices against emerging threats. As IoT technology continues to evolve, the importance of a well-designed and properly executed remote software download strategy will only increase.